Documentation
-
MAGERIT version 3 (spanish version): Analysis and Risk management information systems.
- Edit: © Ministry of finance and Public Administrations 2012.-, october
NIPO
30-12-171 -8: 6
 Book I: method (PDF-1,47 MB)
Book I: method (PDF-1,47 MB)

 Book II: Catalogue of elements (PDF-3,37 MB)
Book II: Catalogue of elements (PDF-3,37 MB)

 Volume III: Technical Guide (PDF-1,28 MB)
Volume III: Technical Guide (PDF-1,28 MB)

 Book I: Method (PDF-1,44 MB)
Book I: Method (PDF-1,44 MB)

 Book I: Method (EPUB-2,94 MB)
Book I: Method (EPUB-2,94 MB)

-
MAGERIT V.2 (English version): Methodology for Information Systems Risk Analysis and Management
.- Edits: © MAP, june 2006
NIPO
26-06-044 -8: 3
 Book I: Method (PDF-1,17 MB)
Book I: Method (PDF-1,17 MB)

 Book II: Catalogue (PDF-270 KB)
Book II: Catalogue (PDF-270 KB)

 Book III: Techniques (PDF-157 KB)
Book III: Techniques (PDF-157 KB)

 Book I: Method (PDF-1,56 MB)
Book I: Method (PDF-1,56 MB)

Introduction
MAGERIT
version 3 is the analytical methodology and risk management developed by former supreme council of E-government and currently maintained by the secretariat-General for administration Digital (Ministry of economic and Digital Transformation) with the collaboration of the centre National Cryptologic (
CCN
).
MAGERIT
it is a public methodology that can be used freely and did not require prior permission. Is mainly addressed to the entities in the scope of the National security scheme (NHIS)
to meet the principle of security management based on risks, as well as the requirement analysis and risk management, considering the information to carry out missions, provide services and achieving the objectives of the organization.
Following the terminology of the rules
ISO 31000, MAGERIT
responds to what is called “ risk management process ”, section 4.4 (“ Implementation of risk management ”) within the “ risk management framework ”. In other words,
MAGERIT
implements the risk management process within a framework of the organs of government decisions in the light of the risks arising from the use of information technologies. 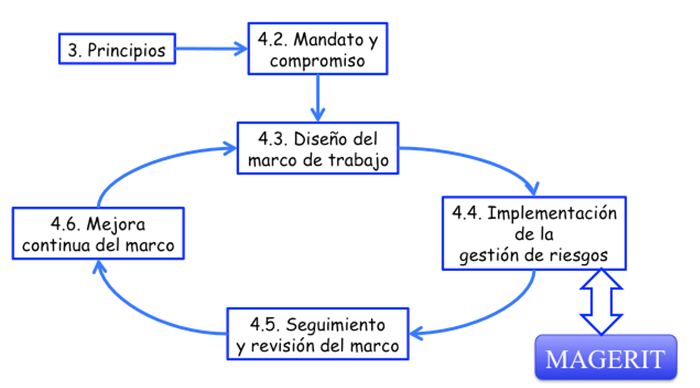
Figure 1. ISO 31000 - framework for risk management
MAGERIT
contained in the inventory of methods of analysis and risk management
ENISA.
Complementary products and services
PILAR it is a tool which implements the methodology
MAGERIT
analysis and risk management, developed by the Centre National Cryptologic (
CCN
), widely-used in the spanish government.
it is a tool which implements the methodology
MAGERIT
analysis and risk management, developed by the Centre National Cryptologic (
CCN
), widely-used in the spanish government.
The agencies of the spanish government can obtain a licence free of charge to the Centre National Cryptologic, point your application to National Cryptologic Centre
ccn@cni.es
Objectives
MAGERIT pursues the following Targets:
- Raising the awareness of the organizations of reports of the existence of risks and the need to manage
- Provide a systematic approach to analyse risks from the use of information and communications technology (ICT)
- Help discover and plan the appropriate treatment to maintain the risks under Indirect control
- Prepare the Organization for processes of evaluation, audit, certification and accreditation, as appropriate in each case
Organization of the guides
MAGERIT version 3 is structured into three books: "" Method, "Catalogue of Elements and" "Guide" Techniques.
Method
Is structured as follows:
- Chapter 2 presents the concepts informally. In particular fall analysis and treatment within a comprehensive process of risk management.
- Chapter 3 concrete steps and formalizes the analysis of risks.
- Chapter 4 describes options and approaches of treatment of risks and formalises the risk management activities.
- Chapter 5 focuses on the draft risk analysis, projects in which we will be plunged to conduct the first risk analysis of a system and if and when there are substantial changes and redo the model widely.
- Chapter 6 formalises the activities of the security plans, sometimes called master plans or strategic plans.
- Chapter 7 focuses on the development of information systems and how the risk analysis serves to manage security of the final product from conception up to its start up, as well as to the protection of the development process.
- Chapter 8 anticipates to some problems that appear recurrent when you are performing risk analysis.
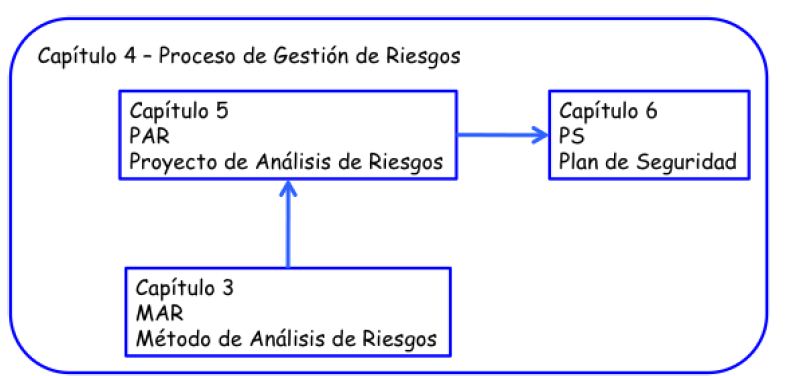
Appendices contain reference materials:
- A glossary,
- Bibliographical references that were being considered for the development of this methodology,
- References to the legal framework that embodies the tasks of analysis and management in the Spanish Government,
- The normative framework for evaluating and certifying
- The characteristics required of the tools, present or future, to support the process of analysis and risk management,
- A comparative guide how Magerit version 1 has evolved to version 2 and to this version 3
List of Elements
Lays down guidelines on:
- Types of assets
- Dimensions of valuation of assets
- Criteria for valuation of assets
- Typical threats on the information systems
- Safeguards to protect to consider information systems
Has two objectives:
- On the one hand, to facilitate the work of the persons undertaking the project, within the meaning of offering standard elements to which they can quickly adscribirse, focusing on what was specific to the system under consideration.
- On the other to harmonise the results of analyses, terminology and standard criteria that make it possible to compare and even to integrate analysis made by various teams.
Each section includes a XML notation used to publish regularly elements in a standard format can be processed automatically by tools for analysis and management.
If the reader uses a tool of analysis and risk management, this catalogue will be part of the same; if the analysis is done manually, this catalogue provides a broad basis to move quickly without disturbances or gaps.
Technical guide
Additional add light and guidance on some techniques that are routinely used to carry out projects of analysis and risk management:
- Specific techniques for risk analysis
- Analysis by tables
- The algorithm analysis
- Attack trees
- General technical
- Graphic techniques
- Working sessions: interviews, meetings and presentations
Valuation Delphi is a reference guide. According to the readers to progress by the tasks of the project, it will recommend the use of certain specific techniques, this guide seeks to be an introduction, as well as to provide references for the reader to comment on the techniques provided.
Experiences applying Magerit
Example of implementation of Magerit version 2, together with the tool Pillar:
Rights to use
MAGERIT, a methodology of a public nature, can be used freely and did not require prior permission. In any exploitation of the work reflected the original authorship.
Responsible for the product
Secretariat-General for administration.
![]() Book II: Catalogue of elements (PDF-3,37 MB)
Book II: Catalogue of elements (PDF-3,37 MB)

![]() Volume III: Technical Guide (PDF-1,28 MB)
Volume III: Technical Guide (PDF-1,28 MB)

![]() Book I: Method (PDF-1,44 MB)
Book I: Method (PDF-1,44 MB)

 Book I: Method (EPUB-2,94 MB)
Book I: Method (EPUB-2,94 MB)

![]() Book II: Catalogue (PDF-270 KB)
Book II: Catalogue (PDF-270 KB)

![]() Book III: Techniques (PDF-157 KB)
Book III: Techniques (PDF-157 KB)














